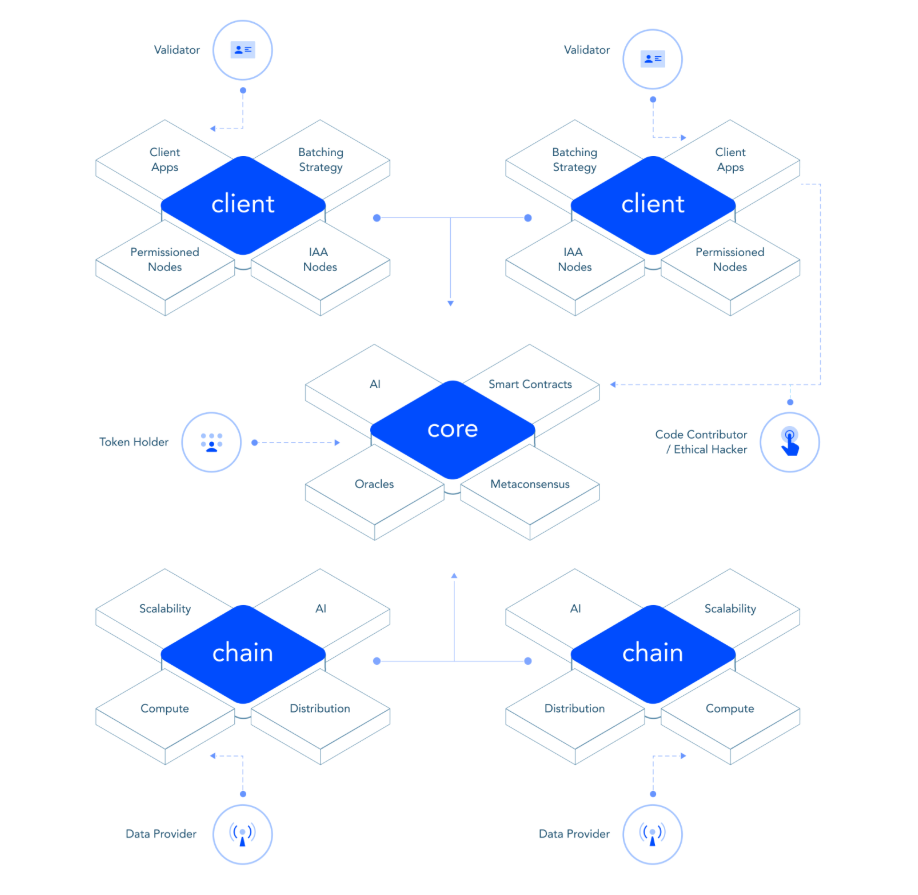
We are a community of passionate individuals who share a common mission: to reinvent transparency for the age of mistrust. Among us are some of the world’s leading experts in cybersecurity, compliance, cryptography, policy, economics and ethics.
Together we are building a blockchain platform and a product ecosystem that combine next-generation innovations in distributed ledger technologies, zero-knowledge proofs, meta-consensus protocols, artificial intelligence, IoT analytics, SaaS functionality and machine learning.